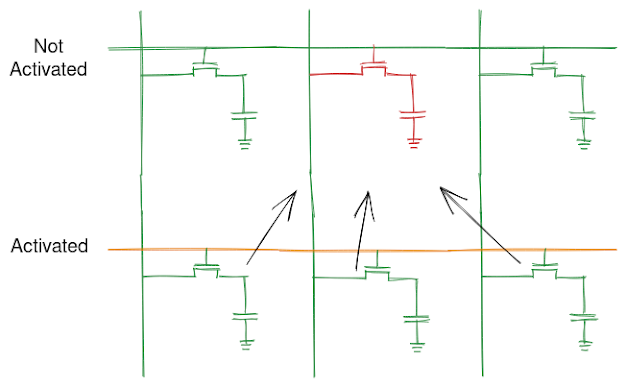
RowClone: Fast and energy-efficient in-DRAM bulk data copy and initialization

In this post, we'll take a brief look at the paper: V. Seshadri et al., "RowClone: Fast and energy-efficient in-DRAM bulk data copy and initialization," 2013 46th Annual IEEE/ACM International Symposium on Microarchitecture (MICRO), 2013 (Link opens a new tab with PDF ~ 2.4MB) IEEE Page (link opens a new tab): https://ieeexplore.ieee.org/document/7847625 This post only takes a brief look at the concept described in the paper and I highly encourage you all to go through the paper to know more about the concept and the underlying mechanism that enables RowClone. Alt: A diagram that illustrates RowClone that uses to back to back activates to clone data from one DRAM row to another using the Row Buffer The picture is made using https://excalidraw.com/ (link will open a new tab) Structure of DRAM If you have read my previous posts on Processing using Memory or Row Hammer, you can skip this section. For those who are new to the blog or are interested in a quick refresh, let u...